Getting Started
Falco is a cloud-native security tool. It provides near real-time threat detection for cloud, container, and Kubernetes workloads by leveraging runtime insights. Falco can monitor events from various sources, including the Linux kernel, and enrich them with metadata from the Kubernetes API server, container runtime, and more.
Once Falco has received these events, it compares them to a set of rules to determine if the actions being performed need further investigation. If they do, Falco can forward the output to multiple different endpoints either natively (syslog, stdout, HTTPS, and gRPC endpoints) or with the help of Falcosidekick, a companion tool that offers integrations to several different applications and services.
Falco Architecture
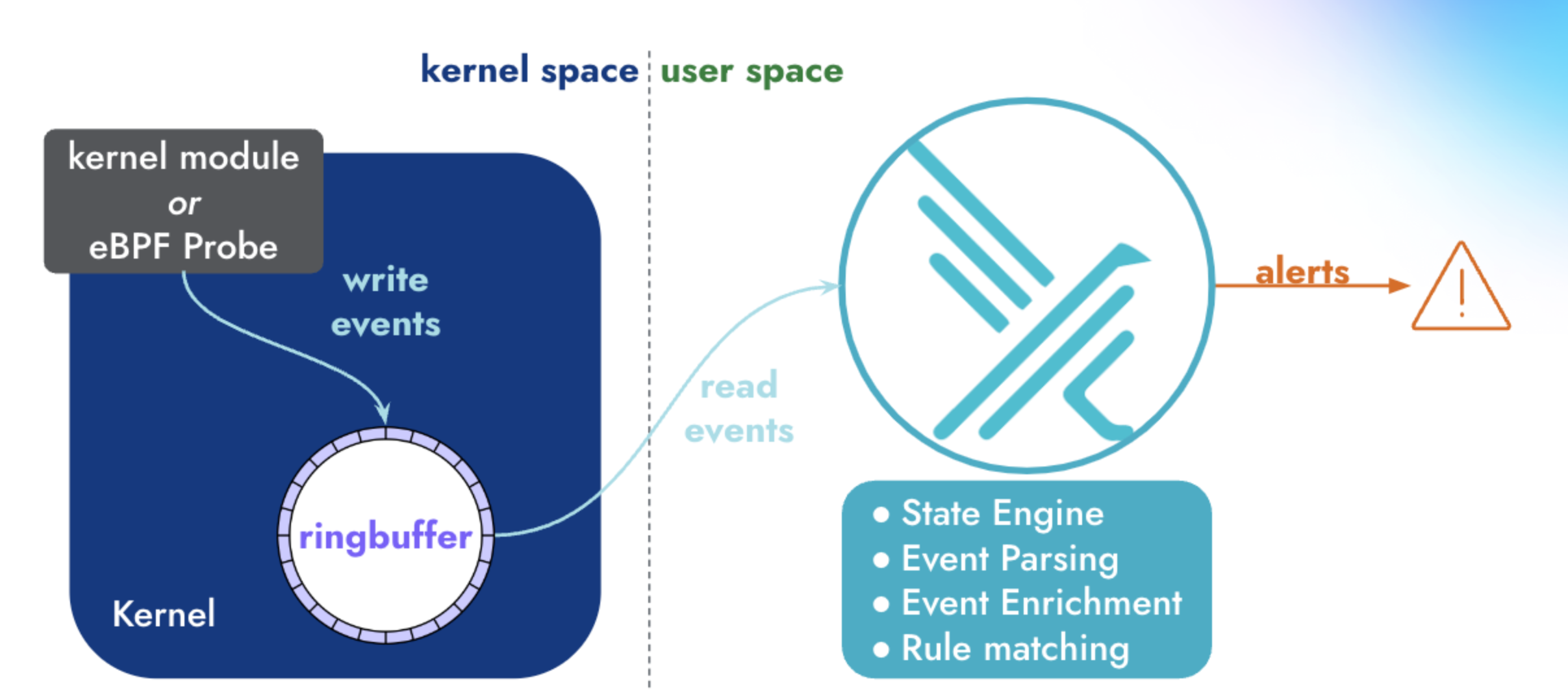
Falco operates in both kernel and user space. In kernel space, Linux system calls (syscalls) are collected by a driver, for example, the Falco kernel module or Falco eBPF probe. Next, syscalls are placed in a ring buffer from which they are moved into user space for processing. The events are filtered using a rules engine with a Falco rule set. Falco ships with a default set of rules, but operators can modify or turn off those rules and add their own. If Falco detects any suspicious events those are forwarded to various endpoints.
Next Steps
A great next step would be to try Falco yourself. The quickstart below walks through how to get Falco running on a Linux host, create a suspicious event, and then check the Falco output.
Try Falco on Linux
Learn how to install Falco on Linux
Try Falco on Kubernetes
Learn how to deploy Falco on Kubernetes
Additional Resources
Learn More About Falco
Was this page helpful?
Let us know! You feedback will help us to improve the content and to stay in touch with our users.
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.
