Blog
Do you have something to share? Contribute to Falco blog!
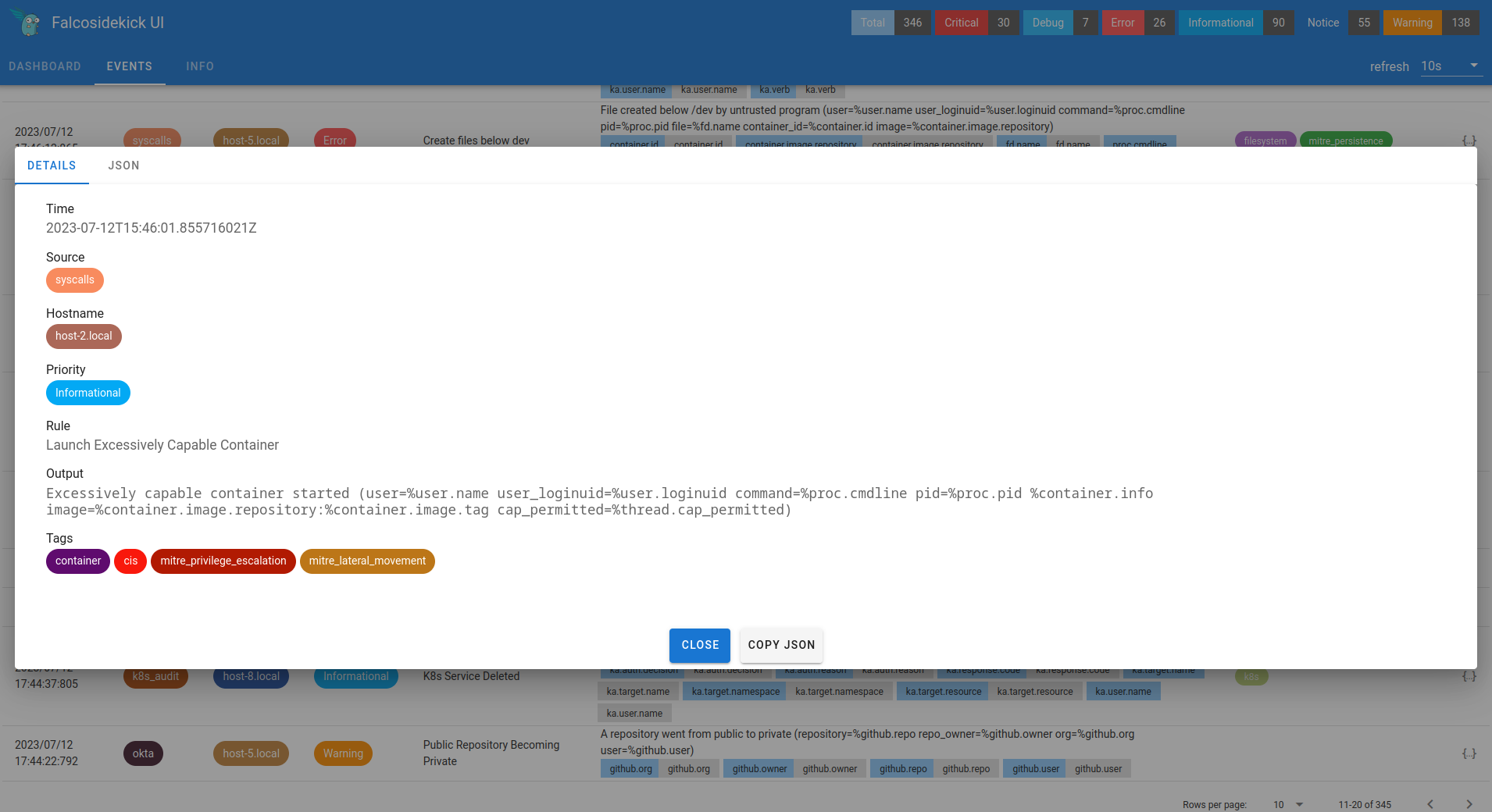
Falcosidekick-UI 2.2.0
Not so long ago, we proudly released a new fantastic release of falcosidekick, it's time for its little brother, falcosidekick-ui to know the same, with the version v2.2.0. Let's take a tour to introduce the most important cool new features …
Tracing System Calls Using eBPF - Part 1
Introduction: In this article, we will delve into the details of eBPF (extended Berkeley Packet Filter) and explore its significance in tracing system calls. This particular blog will be in two parts; in the first blog, we will discuss …
GitLab Container Registry now supports Falcoctl OCI Artifacts
Today, we'd like to share with the Falco community the latest contribution we (w/Emin Aktas) made to GitLab Container Registry. We noticed that GitLab Container Registry didn't support Falcoctl OCI Artifact mediaTypes while we were pushing …
Validating NIST Requirements with Falco
The NIST organization, a non-regulatory federal agency in the United States, plays a crucial role in establishing guidelines across various domains, including cybersecurity. In this article, we focus on NIST 800-171 compliance checks, which …
Crafting Falco Rules With MITRE ATT&CK
Introduction: The landscape of cybersecurity attacks has witnessed a notable rise in sophistication and complexity over the last decade, posing significant challenges to organizations in their efforts to identify and counter such threats …
Understanding PCI/DSS Controls with Falco
As organizations increasingly adopt cloud-native systems for sensitive data and operations, ensuring compliance with industry standards like the Payment Card Industry Data Security Standard (PCI DSS) becomes imperative. This standard is …